Trézor Hardware Wallet: Unmatched Security for Your Crypto Holdings
How the Trézor Hardware Wallet Protects Your Funds
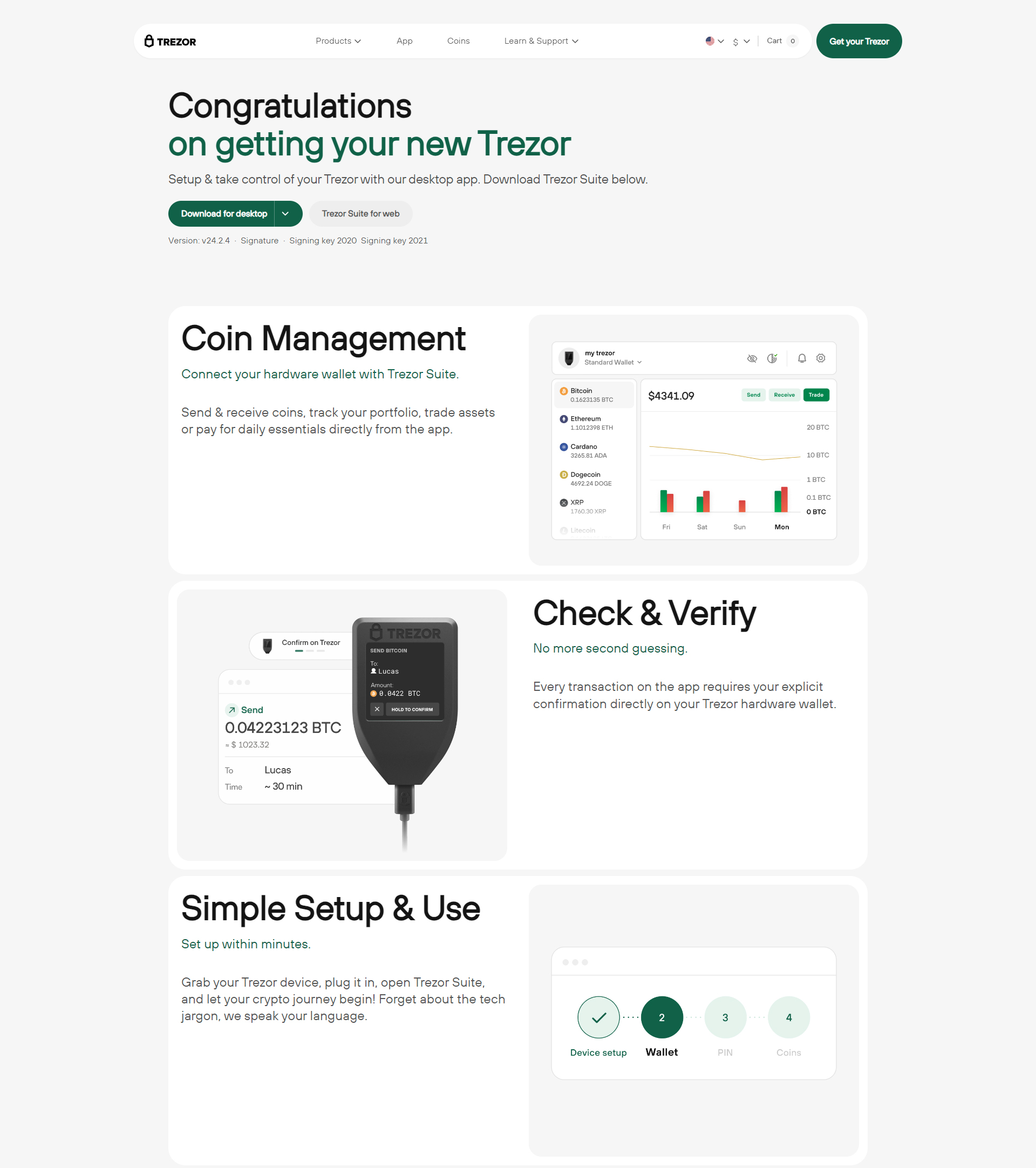
The Trézor Hardware Wallet is built to secure your digital wealth by storing your private keys offline. Unlike software wallets that stay connected to the internet, Trézor isolates your sensitive data, preventing remote attacks, phishing attempts, and malware threats.
Offline Wallet, Maximum Protection
Cold Storage at Its Best
The Trézor wallet keeps your private keys in an offline environment. This separation ensures your cryptocurrencies are protected even if your internet-connected device becomes compromised.
Zero Trust in the Host Environment
Even if you plug your Trézor device into a potentially infected computer, the wallet’s architecture ensures that no private information is exposed.
Start with Confidence: Go to Trézor.io/start
Secure Setup Process
Setting up your Trézor begins at Trézor.io/start, where users are guided step-by-step through initializing the device, setting a PIN, updating firmware, and creating a recovery seed.
Important Setup Steps
- Confirm your device is genuine
- Generate a 12 or 24-word recovery phrase
- Write down your seed and store it securely offline
- Set a unique PIN to block unauthorized access
Why Trézor.io/start Matters
Only through Trézor.io/start can you ensure you're not using a counterfeit or previously compromised device. Always avoid third-party tools during initialization.
Managing Crypto Easily via Trézor Suite
Everything in One Place
Trézor Suite is the official application for managing your crypto portfolio. It’s available as a secure desktop application and a web interface, giving you access to your assets while maintaining cold-storage protection.
Features of Trézor Suite
- Send, receive, and exchange cryptocurrencies
- View real-time portfolio analytics
- Enable Tor for private usage
- Utilize coin control for better fee management
User-Friendly and Secure
All transactions initiated in Trézor Suite require manual confirmation on your hardware device. This minimizes any risk from phishing or browser-based attacks.
Trézor Bridge: The Secure Link Between Device and Browser
What Is Trézor Bridge?
Trézor Bridge is a communication tool that allows your browser to interact securely with your Trézor device. It’s essential if you use browser wallets or third-party applications like MetaMask in combination with Trézor.
When and Why to Use It
When using Trézor Suite in a web browser, Trézor Bridge ensures secure access to your device. Without it, your device might not be detected.
Installing Trézor Bridge
- Download directly from Trézor.io/start
- Choose the version matching your OS (Windows, macOS, Linux)
- Restart your browser after installation
Once installed, Bridge works silently in the background to provide uninterrupted access.
Built for Long-Term Security
PIN and Passphrase Protection
Your Trézor Hardware Wallet requires a unique PIN to unlock. You can also add a passphrase to your recovery seed, creating an extra layer of protection if your seed phrase is ever exposed.
Open Source Transparency
Trézor’s firmware and software are fully open source. This means the global developer community can continuously audit and improve the code, offering unmatched transparency.
Firmware Updates for Continuous Security
Firmware updates are crucial for staying protected. Every update includes bug fixes, improved support for coins, and security patches. Updates can only be installed via Trézor Suite, requiring device confirmation for every action.
Supports a Wide Range of Cryptocurrencies
Popular Coins and Tokens
The Trézor Hardware Wallet supports:
- Bitcoin (BTC)
- Ethereum (ETH)
- Binance Coin (BNB)
- ERC-20 tokens
- Cardano (ADA), Dogecoin (DOGE), and others
Over 1000 coins and tokens are available, with new assets added through firmware updates.
Integration with External Wallets and Apps
You can also connect Trézor to:
- MetaMask
- MyEtherWallet
- Electrum
- Exodus
This flexibility expands Trézor’s usability while keeping your keys secure on the hardware.
Trézor Security Protocols in Action
Manual Transaction Verification
Every transaction must be reviewed and approved on the device itself. Even if malware is present on your computer, no funds can move without your manual approval.
Backup and Recovery Best Practices
When setting up your wallet, always store your recovery seed in a safe, offline location. Consider using metal backup plates for durability. Never take a digital photo of your seed or store it in the cloud.
What Happens If You Lose Your Device?
Even if your Trézor wallet is lost or destroyed, you can recover your assets using the recovery seed on a new device. This makes the seed the single most important component of your crypto security.
Avoiding Common Mistakes with Trézor
Do Not Share Your Recovery Seed
This seed gives full access to your funds. Anyone who has it can restore your wallet and steal your crypto. Never input your seed into websites, emails, or online forms.
Only Buy from Trusted Sources
Purchase your Trézor wallet only from trezor.io or authorized resellers. Avoid buying from marketplaces or second-hand sources, as the device could be tampered with.
Install Trézor Bridge Early
Users often forget to install Trézor Bridge, which results in device connection issues. Install it as soon as you begin the setup process at Trézor.io/start.
Conclusion: Trézor Hardware Wallet Is the Gold Standard
The Trézor Hardware Wallet offers best-in-class protection for cryptocurrency holders. Combined with Trézor Suite and Trézor Bridge, it creates a comprehensive ecosystem for secure, user-friendly crypto management.
Whether you are new to crypto or managing a diverse portfolio, Trézor’s transparent, secure, and open-source platform stands out as one of the safest choices available. Begin your journey confidently by starting at Trézor.io/start and taking control of your digital wealth.